Mastering RemoteIoT Firewall Tutorial: Your Ultimate Guide To Secure IoT Networks
When it comes to securing your IoT devices, the RemoteIoT firewall is your best friend in the digital jungle. Imagine this: your smart home devices, connected cars, or industrial sensors are like unlocked doors waiting for hackers to sneak in. But with a RemoteIoT firewall tutorial, you can lock those doors tighter than Fort Knox. This isn’t just about tech; it’s about protecting what matters most—your data, privacy, and peace of mind.
Nowadays, IoT (Internet of Things) devices are everywhere, from your fridge to your thermostat. But as cool as they are, they also open up a world of vulnerabilities. That’s where RemoteIoT firewall comes into play. It’s not just another tech buzzword; it’s a game-changer in cybersecurity. Think of it as the bouncer at a club, deciding who gets in and who stays out.
In this article, we’ll dive deep into the world of RemoteIoT firewalls, breaking down everything from setup to advanced configurations. Whether you’re a tech enthusiast or just someone trying to keep their smart home safe, this tutorial will give you the tools you need. Let’s get started and make sure your IoT devices are as secure as possible.
- Miguel Love Island Usa The Ultimate Guide To His Journey Impact And Legacy
- Movierulz Com Kannada Movies Download Your Ultimate Guide To Streaming And Downloading
Table of Contents
- What is RemoteIoT Firewall?
- Why RemoteIoT Firewall Matters
- Getting Started with RemoteIoT Firewall
- Installation Guide
- Configuration Basics
- Advanced Features
- Troubleshooting Common Issues
- Best Practices for Security
- Real-World Applications
- The Future of RemoteIoT Firewall
What is RemoteIoT Firewall?
Let’s start with the basics. A RemoteIoT firewall is like a digital guardian for all your IoT devices. It sits between your devices and the internet, filtering out unwanted traffic and blocking potential threats. Unlike traditional firewalls, RemoteIoT firewalls are specifically designed to handle the unique challenges of IoT networks, such as device diversity and limited processing power.
Now, why does this matter? Well, IoT devices are often less secure than regular computers. They’re built to be convenient, not necessarily secure. That’s where RemoteIoT firewall steps in, ensuring that your smart devices don’t become an easy target for hackers. It’s like giving your IoT network a personal bodyguard.
Key Features of RemoteIoT Firewall
Here’s what makes RemoteIoT firewall stand out:
- Anjali Arora Leaked Unveiling The Truth Behind The Viral Sensation
- Unveiling Filmy4wap New Your Ultimate Movie Hub
- Device-Specific Rules: You can create custom rules for each IoT device, ensuring that only necessary traffic gets through.
- Real-Time Monitoring: Get instant alerts if something suspicious is happening on your network.
- Cloud Integration: Many RemoteIoT firewalls can be managed from the cloud, making it easy to monitor and control your network from anywhere.
These features make RemoteIoT firewall a must-have for anyone serious about IoT security.
Why RemoteIoT Firewall Matters
In today’s hyper-connected world, IoT devices are everywhere. From smart thermostats to wearable fitness trackers, these gadgets make our lives easier. But they also come with risks. According to a recent study by cybersecurity experts, over 70% of IoT devices have at least one critical vulnerability. Yikes!
That’s where RemoteIoT firewall comes in. It helps mitigate these risks by:
- Blocking unauthorized access to your devices.
- Filtering out malicious traffic before it reaches your network.
- Providing real-time alerts for potential threats.
Think of it this way: without a firewall, your IoT devices are like an open door. With RemoteIoT firewall, you’ve got a steel-reinforced door with a state-of-the-art lock. It’s that important.
RemoteIoT Firewall vs. Traditional Firewalls
While traditional firewalls are great for computers and servers, they often fall short when it comes to IoT devices. Here’s why RemoteIoT firewall is different:
- IoT-Specific Rules: Traditional firewalls don’t always understand the unique needs of IoT devices.
- Lightweight Design: RemoteIoT firewalls are optimized for devices with limited processing power.
- Easy Management: Most RemoteIoT firewalls come with intuitive dashboards that make setup and management a breeze.
These differences make RemoteIoT firewall the ideal choice for securing your IoT network.
Getting Started with RemoteIoT Firewall
Ready to dive in? Great! The first step in mastering RemoteIoT firewall is understanding the basics. Think of it like learning to drive—a little knowledge goes a long way. Here’s what you need to know:
First, you’ll need to choose the right RemoteIoT firewall for your needs. There are plenty of options out there, from open-source solutions to enterprise-grade software. Some popular choices include:
- pfSense
- OPNsense
- OpenWrt
Each of these has its own strengths and weaknesses, so do your research before making a decision. Once you’ve chosen a firewall, it’s time to move on to installation.
Choosing the Right RemoteIoT Firewall
Picking the right firewall can feel overwhelming, but it doesn’t have to be. Here are a few things to consider:
- Device Compatibility: Make sure the firewall you choose works with all your IoT devices.
- Ease of Use: If you’re not a tech wizard, look for a firewall with a user-friendly interface.
- Cost: Some firewalls are free, while others come with a price tag. Decide how much you’re willing to spend.
By taking these factors into account, you’ll be able to find a RemoteIoT firewall that meets your needs.
Installation Guide
Now that you’ve chosen your RemoteIoT firewall, it’s time to install it. Don’t worry; it’s not as scary as it sounds. Follow these simple steps, and you’ll have your firewall up and running in no time.
Step 1: Download the software. Most RemoteIoT firewalls are available as downloadable packages. Simply visit the official website and grab the latest version.
Step 2: Install the software on your router or dedicated hardware. This step may vary depending on the firewall you’re using, so be sure to consult the official documentation.
Step 3: Configure the firewall. Once the software is installed, log in to the admin panel and start setting up your rules. This is where things get interesting!
Tips for a Smooth Installation
Here are a few tips to make the installation process go smoothly:
- Backup Your Settings: Before making any changes, back up your current router settings. That way, you can restore them if something goes wrong.
- Read the Documentation: Each firewall has its own quirks, so make sure you read the official docs before diving in.
- Start Small: Begin with basic rules and gradually add more complexity as you get comfortable.
With these tips in mind, you’ll be a pro in no time.
Configuration Basics
Once your RemoteIoT firewall is installed, it’s time to configure it. This is where the magic happens. Think of configuration as teaching your firewall what to do and what not to do. Here are some basics to get you started:
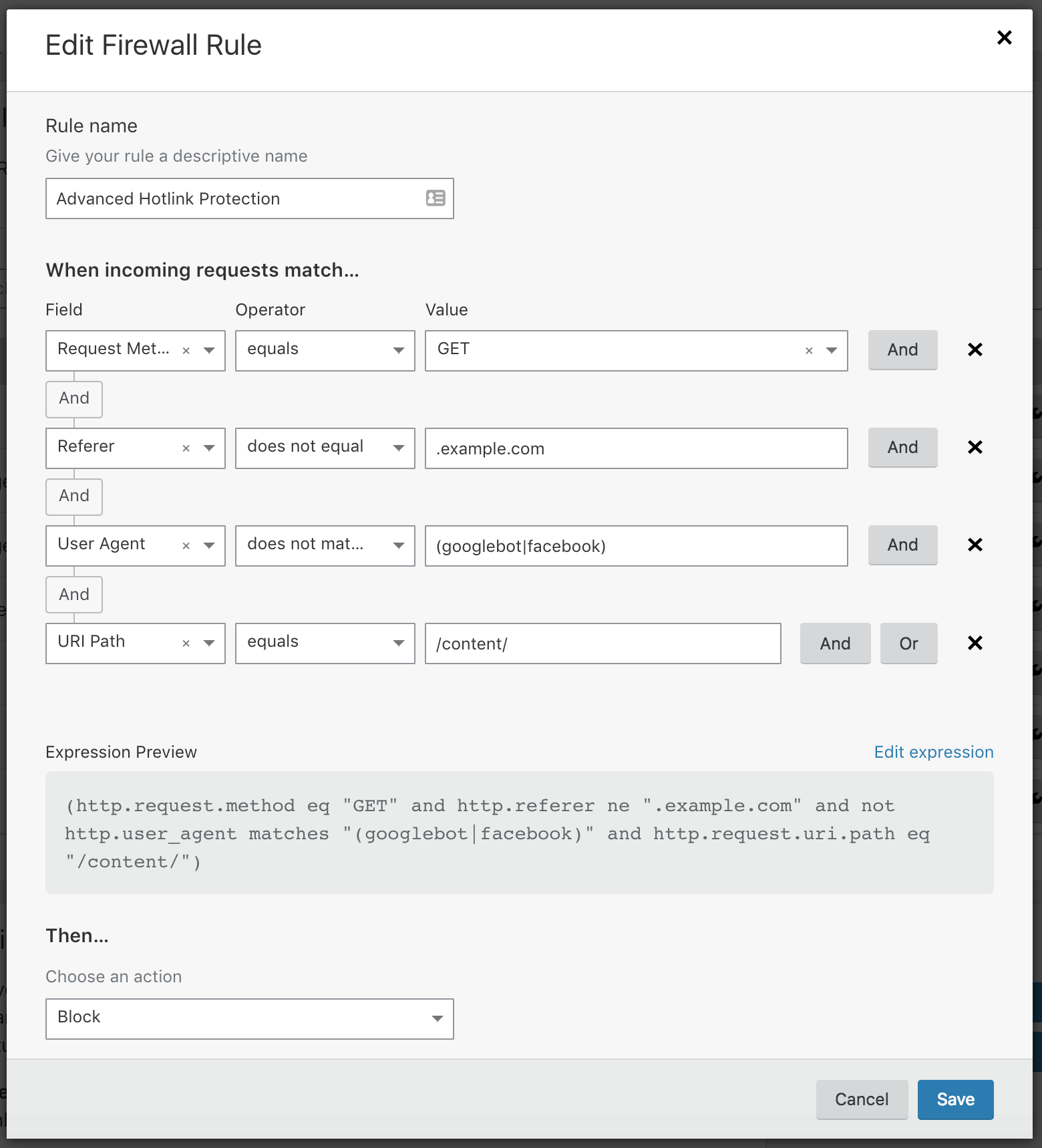
First, create rules for each of your IoT devices. For example, you might want to allow your smart thermostat to communicate with its cloud server but block all other traffic. This ensures that only necessary data gets through.
Next, set up alerts for suspicious activity. Most RemoteIoT firewalls allow you to configure email or SMS notifications when something unusual happens on your network. This way, you’ll know if someone’s trying to hack into your devices.
Creating Device-Specific Rules
Device-specific rules are the bread and butter of RemoteIoT firewall configuration. Here’s how to create them:
- Identify Your Devices: Start by listing all the IoT devices on your network.
- Define Allowed Traffic: For each device, specify which types of traffic are allowed.
- Block Everything Else: By default, block all other traffic to ensure maximum security.
These rules will help keep your IoT devices safe and secure.
Advanced Features
Once you’ve mastered the basics, it’s time to explore some advanced features. RemoteIoT firewalls offer a wide range of tools to help you fine-tune your security settings. Here are a few to consider:
First, look into intrusion detection systems (IDS). These systems monitor your network for signs of malicious activity and alert you when something suspicious is detected. It’s like having a security guard on patrol 24/7.
Next, consider implementing deep packet inspection (DPI). This feature allows your firewall to inspect the contents of data packets, ensuring that only legitimate traffic gets through. It’s a powerful tool for blocking malware and other threats.
Taking Your Security to the Next Level
Here are a few more advanced features to explore:
- Virtual Private Networks (VPNs): Use a VPN to encrypt your traffic and protect it from prying eyes.
- Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of authentication for access.
- Automated Updates: Enable automatic updates to ensure your firewall always has the latest security patches.
By leveraging these advanced features, you’ll be able to take your IoT security to the next level.
Troubleshooting Common Issues
Even the best-laid plans can go awry. If you run into issues with your RemoteIoT firewall, don’t panic. Here are some common problems and how to fix them:
Problem 1: Devices can’t connect to the internet. Solution: Check your firewall rules to make sure the necessary traffic is allowed.
Problem 2: Alerts aren’t working. Solution: Verify that your alert settings are configured correctly and test them to ensure they’re functioning as expected.
When All Else Fails
If you’re still having trouble, here’s what to do:
- Consult the Documentation: The official docs often have solutions to common issues.
- Reach Out to Support: Many RemoteIoT firewall vendors offer excellent customer support. Don’t hesitate to ask for help.
- Join Online Communities: There are plenty of forums and Reddit threads dedicated to IoT security. You’re bound to find someone who’s faced the same issue.
With these troubleshooting tips, you’ll be able to resolve most issues on your own.
Best Practices for Security
Finally, let’s talk about best practices for securing your IoT network. These tips will help you stay ahead of the curve and keep your devices safe:
- Regularly Update Firmware: Keep all your IoT devices and firewalls up to date with the latest firmware.
- Use Strong Passwords: Avoid using default passwords and opt for strong, unique ones instead.
- Segment Your Network: Separate your IoT devices from your main network to limit potential damage in case of a breach.
By following these best practices, you’ll significantly reduce the risk of a security breach.
Real-World Applications
Now that you know how to set up and configure a RemoteIoT firewall, let’s look at some real-world applications. From smart homes to industrial IoT, the possibilities are


Detail Author:
- Name : Fredy Mueller
- Username : coby.collins
- Email : wiza.tabitha@gutkowski.biz
- Birthdate : 1970-07-16
- Address : 589 Rolfson Via Apt. 164 Gracebury, MI 27468
- Phone : 559.563.3890
- Company : Kiehn, White and VonRueden
- Job : HVAC Mechanic
- Bio : Qui deleniti et sunt autem vitae eligendi. Dolorem fuga incidunt qui molestiae non non rerum quia. Sed officiis id similique qui eos. Provident dolores ea totam tempore illum dolor omnis.
Socials
tiktok:
- url : https://tiktok.com/@ellsworth_real
- username : ellsworth_real
- bio : Sit saepe ex rerum ratione architecto alias.
- followers : 6665
- following : 2298
linkedin:
- url : https://linkedin.com/in/ellsworth.kuhic
- username : ellsworth.kuhic
- bio : Recusandae ut maiores totam expedita.
- followers : 3025
- following : 817
instagram:
- url : https://instagram.com/ellsworth_dev
- username : ellsworth_dev
- bio : Provident esse magnam et id molestias nesciunt. Explicabo alias eum sint nostrum exercitationem.
- followers : 487
- following : 1184